by Costanza Matteuzzi & Aldo Pedico
In our first part of the article that has been published last week, we discussed the role of the European Union in the field of criminal law, company and personal needs, the requirements of laws, regulations and standards and the implications. Now in this second part, we will discuss the cybersecurity quality system, the paradigm, certification of the cybersecurity quality system process and finally end with a conclusion to our paper.
For some years now, we have witnessed an increasingly strong integration of IT systems both as peripheral platforms for information processing and for quantity and type of data. This integration requires particular attention and care of the data processed and the relative services, deriving above all from the laws in force; according to the writer, this determines an evolution of the term quality.
Cybersecurity Quality System
Historically in the IT context, the term quality has tended to be associated with some features of the software: now this setting has changed! Software quality can no longer be cultivated as an entity detached from other contexts (regulations and laws, technology and services). The need to talk about the Quality System is born. Hence the need for a new Paradigm. This concept contains the following contexts:
1) the data;
2) the software or product;
3) the service and process;
4) the people or roles
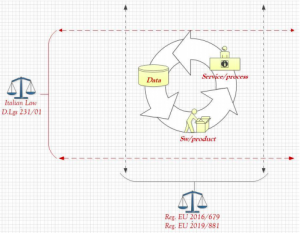
The contexts are elements of the intersection of the laws, which, in the specific case EU Reg. 2016/679 and Ex. Legislative Decree 231/01, refer directly or indirectly to the attributes belonging to the individual contexts. Furthermore, the EU Regulation 2019/881 on Cybersecurity (Cybersecurity Act) was recently published and recital (65) mentions:
“Cybersecurity certification plays an important role in increasing trust and security in ICT products, ICT services and ICT processes. The digital single market, and in particular the data economy and the IoT, can thrive only if there is general public trust that such products, services and processes provide a certain level of cybersecurity. Connected and automated cars, electronic medical devices, industrial automation control systems and smart grids are only some examples of sectors in which certification is already widely used or is likely to be used in the near future. The sectors regulated by Directive (EU) 2016/1148 are also sectors in which cybersecurity certification is critical.”
As a logical consequence, both to the previous affirmation (“Here the Union tends to prepare a strategic program for the exchange of information which presupposes an overview of the current systems for collecting, processing and sharing data, which is accompanied by an in-depth assessment of their usefulness, efficiency, effectiveness, proportionality and observance of the right to respect for life.”) and in the aforementioned recital, the company that produces and sells a product, a service and a process must adopt an IT system through which it assumes both the responsibility for the quality of the data processed and the guarantee of the quality of the process and of the product used for the treatment. Otherwise, if the company does not adopt these “mechanisms” to introduce the principles of responsibility and guarantee in its production system, it is likely to suffer economic damage due to loss of market share.
Instead, the company that acquires a product, a service or a process will have to adopt, in its management system, an internal process that excludes those suppliers that do not assume neither the responsibility of the quality of the treated data nor provide the guarantee of the quality of the process and of the product used for the treatment. Therefore, the union of the principles of Responsibility and Guarantee within a management system is enriched with an extremely important value, namely the adoption of the “Cybersecurity Quality System”. At this point, the new Cybersecurity Quality System Paradigm can be used to incorporate the requirements of the European Union regulations 2016/679 and 2019/881 with the social needs of people, processes, services and products within companies.
Paradigm
Starting from the definitions, we want to indicate how this innovative Paradigm, more suited to current needs and extended to the new European regulations, actually turns into a model. This model outlines the future change both of understanding the reality of facts and relations with others, characteristic of a modern mentality, and of organizational and internal organizational processes within companies.
Definition of Quality System:
Set of concrete elements that are interdependent and organized so as to form an organic complex
Explanation:
The set is composed of the following heterogeneous elements.
A. Technologies
1. Physical infrastructure (network, computers, equipment, etc.)
2. Software, database
B. Techniques
3. Encryption, anonymisation, etc.
4. Software development techniques (vulnerability, efficiency, effectiveness, etc.)
5. Test techniques, protection against risk reduction (SAST, IAST, PT, BAS, WAF, etc.)
C. Rules and Principles
6. Reference standards (ISO/IEC 25000, ISO/IEC 27000, ISO/IEC 29100; NIST; PCI-DSS; OWASP; CWE SANS; etc.)
7. Compliance with laws Reg. EU 2016/679 (GDPR) and Reg. EU 2019/881 (Cybersecurity Act)
8. Policy.
D. Organization
9. Rules for assigning tasks
10. Roles
Quality System = {Technology Ս Technique Ս Rules & Principles Ս Organization}
Summarizing the previous concepts, we obtain the following schemes.
From the previous schemes, it is evident that the Quality System is enriched with the Cybersecurity component to protect both data, processes and services in compliance with the new European regulations. It is necessary to make the following consideration.
Axiom: The Security is Quality Characteristic
To evaluate the Security features of quality, for example of a software product (the same example can be replicated to processes and services with the related ISO/IEC or NIST standards), ISO/IEC 25010 proposes to use the GQM (Goal, Question, Metric). In the detail of the definitions, below, the sub-characteristics of the Quality are listed with reference to the characteristics of the Cybersecurity.
- Prevent => Integrity (It evaluates the ability to protect against unauthorized access to data and information, be this accidental or deliberate)
- Protect => Confidentiality (It evaluates the ability of the system or computer to prevent unauthorized accesses or modifications to computer data or programs)
- Demonstrate => Non-repudiation (It evaluates the ability to prove the actions or events that have taken place so that such actions or events cannot be repudiated later on)
- Responsibility (Activity Tracks) => Responsibility (It evaluates the ability to unequivocally track the actions carried out by an entity)
- Authenticity (illustrate/show) => Authenticity (It evaluates the ability to prove the identity of an individual or a resource)
Combining the definitions of Quality System and Axiom, we obtain: Cybersecurity Quality System Paradigm. From a practical point of view, this Paradigm is resolved with the adoption Certification Processes of Product, Process and Service as, on the other hand, indicated in recital (65) of the EU Regulation 2019/881: “Cybersecurity certification plays an important role in increasing trust and security in ICT products, ICT services and ICT processes. …..”. In the next paragraph, a process of innovation integrated into a Management System, which imposes a radical methodological transformation, is indicated through a scheme.
Certification Of The Cybersecurity Quality System Process
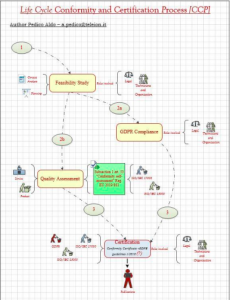
Scheme of the Process or Life Cycle
Steps Description:
Point (1) The evaluation of the feasibility of buying or selling a service, a product or a process must meet the needs imposed by the company.
Point (2a) The verification of the compliance imposed by the EU Reg. 2016/679 of the technical, technological and organizational specifications pertaining to a service, a product or a process supplied. Simultaneously, the process provides for
Point (2b) Verification of the conformity recommended by the EU Regulation 2019/881 of the technical, technological and organizational specifications pertaining to a service, a product or a process supplied. For information, the following is an extract from articles 53 and 56 of the EU Regulation 2019/881.
Article 53 – Conformity self-assessment
1. European cybersecurity certification scheme may allow for the conformity self-assessment under the sole responsibility of the manufacturer or provider of ICT products, ICT services or ICT processes. Conformity self-assessment shall be permitted only in relation to ICT products, ICT services and ICT processes that present a low-risk corresponding to assurance level «basic».2. The manufacturer or provider of ICT products, ICT services or ICT processes may issue an EU statement of conformity stating that the fulfillment of the requirements set out in the scheme has been demonstrated.
By issuing such a statement, the manufacturer or provider of ICT products, ICT services or ICT processes shall assume responsibility for the compliance of the ICT product, ICT service or ICT process with the requirements set out in that scheme. 3. …. 4. The issuing of an EU statement of conformity is voluntary, unless otherwise specified in Union law or Member State law. 5. EU statements of conformity shall be recognised in all Member States.
Article 56 – Cybersecurity certification
1. ICT products, ICT services and ICT processes that have been certified under a European cybersecurity certification scheme adopted pursuant to Article 49 shall be presumed to comply with the requirements of such scheme. 2. The cybersecurity certification shall be voluntary unless otherwise specified by Union law or Member State law.
Point (3) The results of the previous verifications require the supplier to provide for selfcertification or certification based on international standards at the Cybersecurity Quality System. The reference standards are indicated in the table in which they are divided for each context, within the previous paragraph “Paradigm”.
Conclusions
In order to reach the expected quality level, a change in the mindset of companies is prodromal, which tends towards a systematic combination of technique, technology and organization, setting aside the multitude of certifications. Only by raising awareness of a total quality vision that encompasses the whole company, understood and conceived as a unit, and not in individual areas split apart, one can reach and guarantee the security of the data and reach a quality level that meets today’s security requirements under the law.
About the authors: Costanza Matteuzzi is a lawyer, expert in employment law, GDPR and cyber law and Aldo Pedico is project manager/ consultant GDPR and Cybersecurity Act.